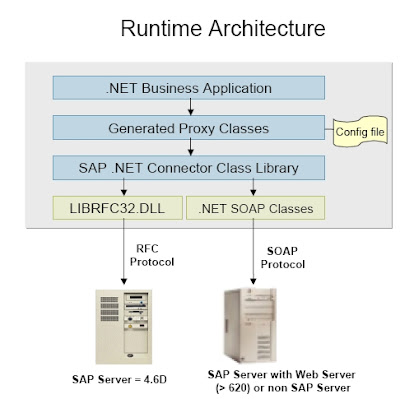
The past few posts, I’ve really concentrated on the Microsoft ERP MA for SAP integration. Although my world revolves around identity management, a huge piece of that I spend on integration of systems throughout the enterprise that do not share a common platform. One of which is SAP. By no means would I consider myself an SAP Consultant; however the need to understand the inner-workings of foreign systems only makes my job that much easier. Surprisingly, SAP is one of those systems we find customers having difficulties integrating into different connected data sources all around the enterprise.
This post will further concentrate on key components of SAP; most typically how SAP communicates to the outside world. From here, you can better understand how to achieve proper integration.
The first thing is to understand some key concepts of SAP. SAP talks through various Business Application Programming Interfaces also known as BAPIs. These interfaces are object-oriented methods which are the data-handling mechanisms used in SAP Systems. Knowledge of how to instantiate these objects are the most powerful tool in an SAP consultant’s arsenal. BAPIs are business objects similar to transactional records, master records, or datasets. They are most used when calling data in and out of SAP. Although out of the box, there are several hundred BAPIs available for use; they can also be customized to fit any business need required.
Another key concept to BAPIs and most often confused are IDocs. IDocs are data transports and are about moving data between systems and modules within SAP. Ultimately, BAPIs are the mechanisms for getting data in and out of SAP; therefore when integrating SAP with MIIS, you will be invoking or passing parameters to BAPIs to retrieve any type of data.
Remote Function Calls (or RFCs) are function modules that are called within a BAPI. They relate to each other as a BAPI is a business object; whereas an RFC is the functional code.
A perfect example of what happens is, (A) you call a BAPI, then (B) pass parameters to invoke RFCs.